Two-Factor Authentication
Two-Factor Authentication (2FA) in TechMaju adds an additional layer of security to the system by requiring users to provide two forms of verification during login. This enhances security by ensuring that access is only granted to authorized users, even if their passwords are compromised.
Understanding Two-Factor Authentication
Purpose: The purpose of 2FA is to secure user accounts by requiring an additional step during login. This reduces the risk of unauthorized access and helps protect sensitive data within the system.
Function: When 2FA is enabled, users will need to enter a One-Time Password (OTP) after entering their username and password. This OTP can be generated via an authentication app, sent via SMS, or sent to the user's email address. The system supports multiple methods for flexibility and convenience.
Role Required
- System Manager: Can create, read, and write System Settings.
Pre-Requisite
- Before enabling Two-Factor Authentication, ensure that an outgoing email account is configured in the system. This is required for sending emails when the Email method is used for authentication or for sending QR code links to setup OTP Apps.
Two-Factor Authentication Fields
| Field | Description |
|---|---|
Enable Two-Factor Auth |
Enables or disables 2FA for the system. |
Bypass Two Factor Auth for users who login from restricted IP Address |
If enabled, users who login from Restricted IP Address, won't be prompted for Two Factor Auth. |
Bypass restricted IP Address check If Two Factor Auth Enabled |
If enabled, all users can login from any IP Address using Two Factor Auth. This can also be set only for specific user(s) in User Page. |
Two-Factor Authentication method |
Determines how the OTP is delivered: OTP App, SMS, or Email. |
Expiry time of QR Code Image Page |
Time in seconds to retain QR code image on server. Min: 240. |
OTP Issuer Name |
Name displayed in the authenticator app when users add their TechMaju 2FA account. |
- 2FA does not apply to Web Users and API login.
- TechMaju uses a TOTP-based OTP algorithm, which depends on the system time of the device being used. It is important to ensure that the device in use has the same time set as the TechMaju server.
Setting up Two-Factor Authentication
Enabling Two-Factor Authentication
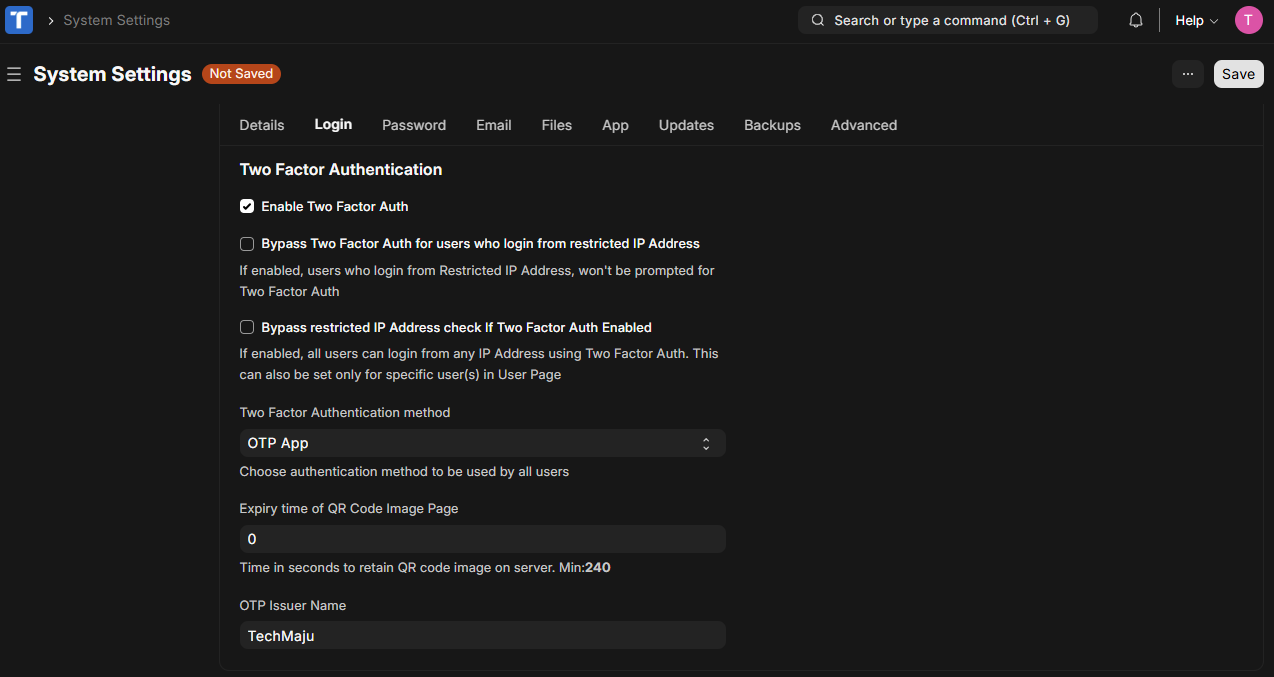
- Search with the Awesomebar for System Settings > Login Tab.
- Enable 2FA:
- Check the Enable Two-Factor Auth checkbox.
- Choose Authentication Method:
- Select the preferred method from the dropdown:
- OTP App: Uses TOTP. Supported apps include:
- Google Authenticator
- FreeOTP
- Lastpass Authenticator
- Authy
- Duo Mobile
- SMS: Sends OTP via SMS.
- Email: Sends OTP to the user's email.
- OTP App: Uses TOTP. Supported apps include:
- Select the preferred method from the dropdown:
- Set Additional Parameters:
- Expiry Time for QR Code Image: Specify the validity period for the QR code when using the OTP app.
- OTP Issuer Name: Enter the organization name (e.g., "TechMaju").
- Save Changes:
- Click Save to apply the changes.
Configuring User Roles
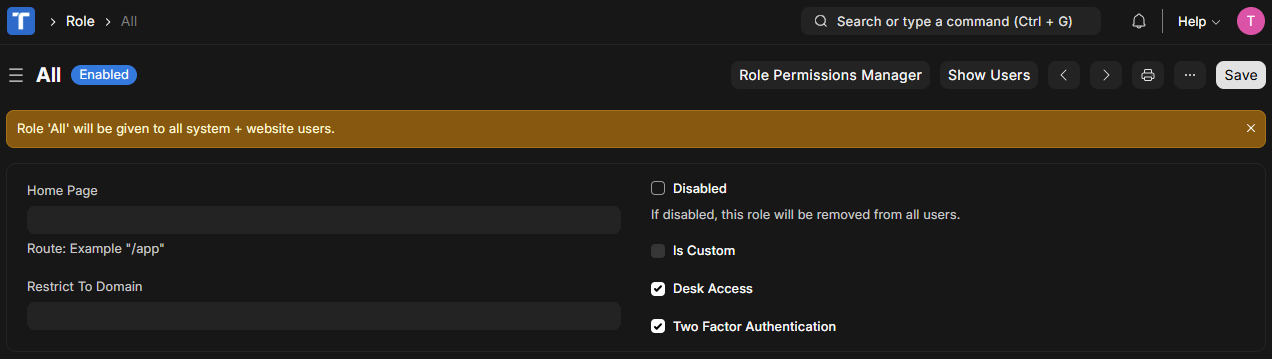
- By default, 2FA applies to all users when enabled.
- To restrict 2FA to specific roles:
- Go to User > Roles > All.
- Uncheck the Enable Two-Factor Auth option for the All role.
- Enable it only for the desired roles.
If the Enable Two-Factor Auth checkbox is unchecked in System Settings then the Two-Factor Auth checkbox has no impact on user login.
Configuring SMS Settings
- If using the SMS method, configure the SMS gateway in SMS Settings.
After 2FA is Enabled
First-Time Setup for OTP App:
- Users must log out and log back in to initiate setup.
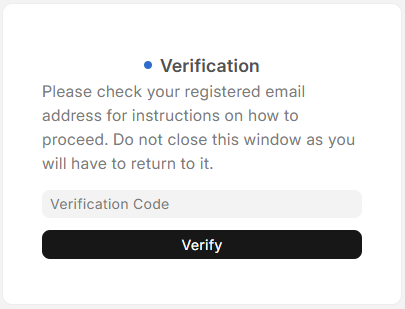
- After entering the login information, a verification message will appear asking the user to check their registered email address for instructions on how to set up the 2FA.
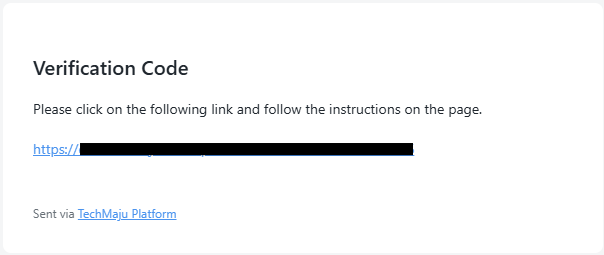
- Users receive an email with a link to a QR code when logging in for the first time.
- They scan this QR code using an authenticator app.
- Then they can go back to the login page and enter the code from the authenticator app.
OTP Prompt on Login:
- After entering their username and password, users are prompted for an OTP to complete the login process.
Testing Two-Factor Authentication
- Log Out and Log In:
- Log out of the system and attempt to log in with the user’s credentials.
- Verify OTP Prompt:
- After entering the user’s username and password, ensure the system will prompt for an OTP.
- Generate and Enter OTP:
- Open the configured method (app, SMS, or email) and retrieve the OTP.
- Enter the OTP to log in.
- Validate Configuration:
- Ensure the OTP validation is smooth and respects any filters or restrictions applied.
Handling Lost Access to Authentication App
Follow this steps when a user lost their access to their Authentication App.
- Access the User’s Record:
- Navigate to Users > User > User’s Record
- Reset OTP Secret:
- Click on the Password button located on the top of the Form.
- Two options will show up: Reset Password and Reset OTP Secret.
- Click on Reset OTP Secret.
- Reconfigure 2FA:
- The user will be prompted to set up 2FA again on their next login.